Recently, I got an opportunity to compare the Private Endpoint for Web Apps, Service Endpoints for Web Apps and App Service Environments. I thought it would be good to write a blog post on the observations and the comparison I learned. Limiting the attack vector for the web applications and exposing the application only to the customer private networks is a very common requirement when you talk to customers. Therefore, this blog is about a comparison between the most commonly used hosting methods for internal-facing web applications in Azure.
Private Endpoints for Web Apps
With the announcement of the Private Endpoints for Web Apps, it opens up a new architecture for making Azure Web Apps available to the Azure Networks. This method creates a Private IP address in your virtual network dedicated for the Web App instance you choose. This private IP can be used as a secure entry point for the Web Application. This feature combined with external access blocked to the web app makes the application available only to the local network.
The traffic originating from an end-user traverse the virtual network to the private endpoint for the web app. Then it goes through the Microsoft Backbone to the Web App. It never goes to the Public Internet. Hence, this is a much secure way to have connectivity to internal-facing web applications.
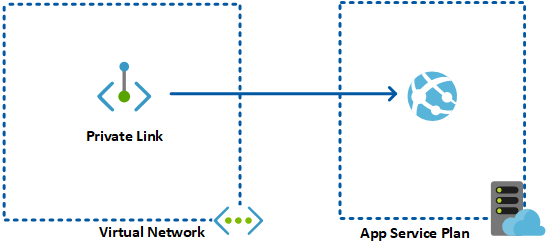
The above diagram shows the high-level architecture for the private endpoint for web apps. One of the key features of this architecture is that this model works with the hybrid networking configuration as well. This means, your on-premises users can route to your web application using the private endpoint in the virtual network. This also provides additional security features. Private endpoint makes sure that only the allowed web application instance can be accessed by the private endpoint. It can not access any other service through it. Therefore, it protects you from any possible data exfiltration from your network.
Note that this feature is still in public preview as of 10/07/2020.
Service Endpoints for Web Apps
Service Endpoints for Web Apps provide secure connectivity to Azure Web apps over an optmized route over the Microsoft backbone. When compared with the Private Endpoints, Service Endpoints does not provide a private IP in your network. Instead, it will add special routes to your VNet, so that the Web App traffic will route via the Microsoft backbone to the web app. Therefore, it will not leave the Microsoft network when reaching the web app. You can also combine Service Endpoints and restrict public access to only allow traffic from the virtual networks selected.
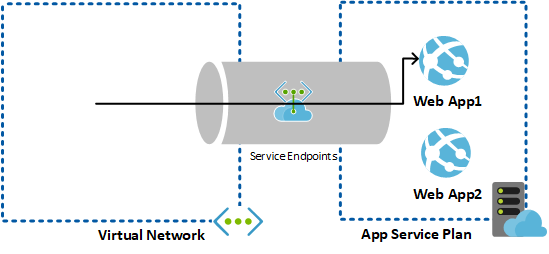
The diagram above shows the high level architecture for the Service Endpoints for web apps. One of the key functional differences in service endpoint, when compared to private endpoints, is that this provides private access to the full service in the Azure Region whereas in Private link it is only to that instance.
Service endpoints are simple to configure and easier option when compared to the other two.
App Service Environments
Azure App Service environments provide a fully isolated and dedicated environment in a customer network to run web apps. This provisions a dedicated instance of the app hosting plan in your network as opposed to the multi-tenanted offerings in the other two option. This allows customers to fully control network traffic that goes in and out of the web app.
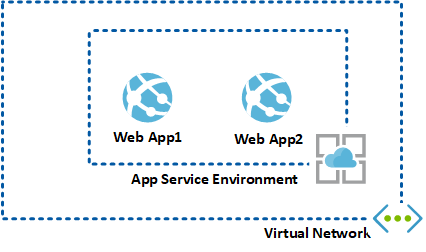
The above high-level architecture diagram shows how the App service environment sits in the network. Providing internal access to the application is easy since it sits within the virtual network. If you have hybrid connectivity via an ExpressRoute or a Site-to-Site VPN, then it can route to the web application without any special configuration.
Summary
In this post, we looked at different architecture options for hosting a Web App which is exposed to the internal network only. See the below table, as a summary of features, functionalities and complexities discussed above.
| Private Endpoints | Service Endpoints | App Service Environments |
|---|---|---|
| Provide Access to Web Apps over Private IP Address | Provide Access to Web Apps over optimized backbone routing | Web Apps are provisioned within the customer network |
| Access is restricted per Web App Instance | Access is restricted per Web app Service | Access restriction up to the customer as the service is in the customer network |
| Complexity: Planning and initial configuration required | Complexity: Easy to setup | Complexity: Planning and Initial configuration required |
| In-built data exfiltration protection | Traffic will need to be passed through an NVA/Firewall for exfiltration protection | N/A as the application is entirely in the customer network |
| Cost compared to the other two options: moderate | Cost compared to the other two options: Can be low and depends on the application | Cost compared to the other two options: Higher running cost |
| Multi-tenant Hosting plan | Multi-tenant Hosting plan | Dedicated hosting plan |
